
Holiday Shopping Alert: How to Avoid New PayPal Payment Scam
If you’re holiday shopping, after holiday shopping, or just purchasing the everyday stuff, there’s a new take on a skimming payment scam affecting PayPal users worldwide. There are 305 million active PayPal accounts globally since the end of last year, with almost 44% of those users in the U.S. This latest skim scam is popping up just in time to steal your gift giving spirit and your money, but being aware of it can help PayPal shoppers avoid becoming the next victim. And if not you, then tell your friends and family about this latest scam and help keep them from being ripped-off.
From all reports, a group known as Magecart is behind this new card-skimming attack method on PayPal users. Magecart is an umbrella term for different threat groups using the same attack method, and it has a long history of targeting e-commerce websites and those who shop on them. Magecart compromises retail checkout pages and steals payment card details and other information added to the page. Now, PayPal has become Magecart’s target for this new card-skimming technique. And those using PayPal to make online purchases are its latest victims.
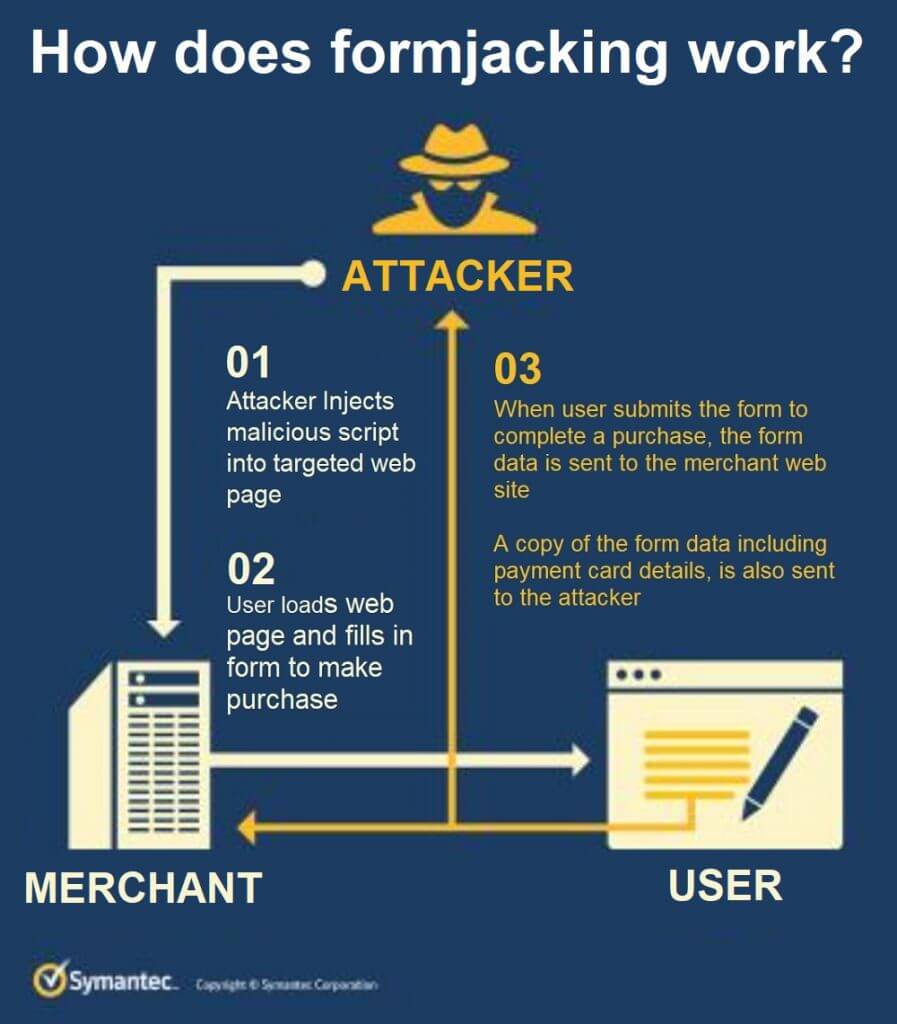
This new take on payment card skimming relies on steganography to work. Simply put, steganography can embed malicious code in files like images, messages, and videos. For this scam, it’s hiding in the PayPal logo on a fake PayPal web page. Once payment information is entered, the skimmer gets to work stealing the data, sending it to the hacker in a remote location. The skimmer then hits the true “order button” underneath the bogus page, sending the victim back to the real checkout page to finish the transaction. It’s all done in the blink of an eye, with the user and retailer being none the wiser.
The good news is there are precautions to keep this and other skimming scams away from your online shopping.
Keeping it real:
- Enable two-factor authentication (2FA) on your PayPal account. The malicious forms do not use 2FA, so this will be a huge red flag.
- Closely check the spelling of the URL. Hacker’s look to fool us with misspellings of the domain name, such as “gooogle.com.” They’re very tricky, so always put the domain spelling under a microscope before continuing.
- Make sure the lock icon is present at the far left of the URL, and the web address starts with “https” and not “http.” Having both present means the site is secure and communication between you and the seller is encrypted and not open to online snoopers.
- Take an overall good look at the web page. Hacker’s may be okay at reproducing the appearance of a page, but even that’s questionable. Blurry logos and other out of place graphics are sometimes common on a bogus web page. And when it comes to spelling and grammar, hackers are even worse. Bad spelling and poor grammar are a dead giveaway that a hacker is behind creating the web page, and it’s a sure sign that you should abandon the page immediately.
From Stickley on Security

